Quantitative Risk Assessment 101
Category
Quantitative Risk, Cybersecurity Fundamentals
Risk Level
“Where do I start?”
Getting started with quantitative risk assessment is easier than you might think.
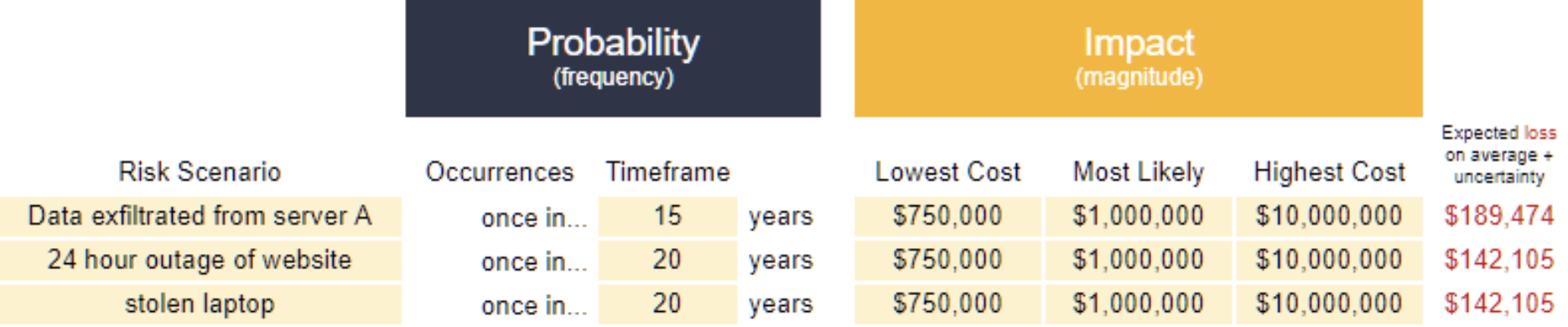
If you’re calling the shots at your organization, drop ordinal scoring (i.e. using 1, 2, 3 or low, moderate, high) entirely and replace it with dollar amount ranges for impacts and frequency ranges for probabilities. For example:
If you’re not calling the shots at your organization, and you can’t convince your stakeholders to go quantitative, ask them if you can run a pilot quantitative risk assessment alongside your next assessment target.
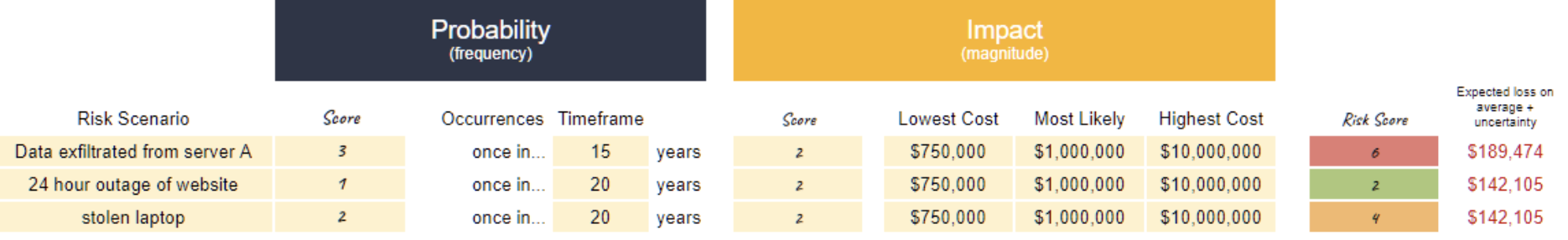
Collect ordinal scores from your estimators like you normally do, but also ask them to provide range estimates.
Add a new column, or columns, next to your risk scores to collect the range estimates, like this:
“Ok got it, but how can I try it out?”
This is the process at a high level, and you can start doing this today! Try out this starter quantitative risk assessment spreadsheet we developed.
If you need some help with quantitative risk assessments, or convincing your decision makers that this is a better way forward, don’t hesitate to contact us. Hive Systems helps organizations from big to small:
Leverage existing resources to go quantitative;
Shift organization practices to quantitative;
Make the case for quantitative to stakeholders; and
Focus on your your strengths while building your foundation for the future.